Cyber Security Fundamentals: Safeguarding Digital Assets

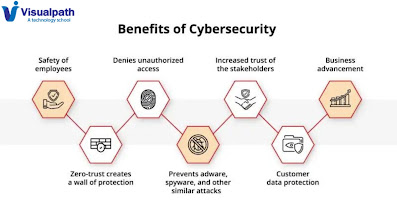
Introduction: Cybersecurity cannot be overstated. From personal information to critical infrastructure, virtually every piece of data is at risk of being compromised by cyber threats. To navigate this landscape safely, it's crucial to understand the fundamentals of cybersecurity and implement effective strategies to safeguard digital assets. - Cyber Security Online Training Nature of Cyber Threats: Cyber threats come in various forms, ranging from common malware such as viruses and ransomware to sophisticated hacking techniques like phishing and social engineering. These threats exploit vulnerabilities in software, networks, and human behavior to gain unauthorized access to sensitive information or disrupt operations. Principles of Cybersecurity: Risk Management: Identifying and assessing potential risks is essential for prioritizing cybersecurity efforts. By understanding the value of data and potential threats, organizations can allocate resources effectively to mi...
.jpg)
