The Importance of Cyber Security

Introduction: Cybersecurity encompasses a broad range of practices and measures designed to protect digital systems, networks, and data from cyber threats, including hacking, malware, and unauthorized access. - Cyber Security Online Training Protecting Sensitive Data: One of the primary reasons why cybersecurity is essential is the protection of sensitive data. From personal information and financial records to intellectual property and trade secrets, our digital lives are filled with valuable data that must be safeguarded from unauthorized access and exploitation. A breach in cybersecurity can result in the theft, manipulation, or exposure of this sensitive information, leading to financial loss, identity theft, and reputational damage. Preserving Trust and Confidence: Cybersecurity also plays a crucial role in preserving trust and confidence in digital systems and services. As consumers, we rely on technology for a wide range of activities, including online banking, shop...


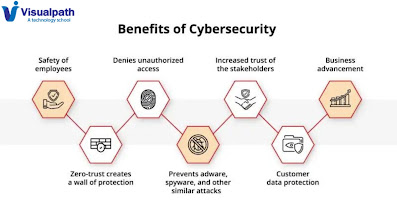
.jpg)
